Call from NIDS: The Cybersecurity Threat Explained Every cybersecurity threat explained
If you are looking for HIDS vs NIDS —What’s the Difference and Why Should I Care? | by you've visit to the right page. We have 25 Pictures about HIDS vs NIDS —What’s the Difference and Why Should I Care? | by like VR Headsets Explained: A Beginner's Guide to How They Work - YouTube, Comparison Between NIDS And NIPS Cybersecurity Framework and also Threat modeling explained: A process for anticipating cyber attacks. Read more:
HIDS Vs NIDS —What’s The Difference And Why Should I Care? | By
 medium.com
medium.com
NIDS: Jamaica's Controversial NIDS System Explained | National
 www.youtube.com
www.youtube.com
Insider Threat Awareness Exam Answers 2024 Insider Threat Aw
 gairotaodqlessonmedia.z14.web.core.windows.net
gairotaodqlessonmedia.z14.web.core.windows.net
What Is Threat Modeling? (+Top Threat Model Examples)
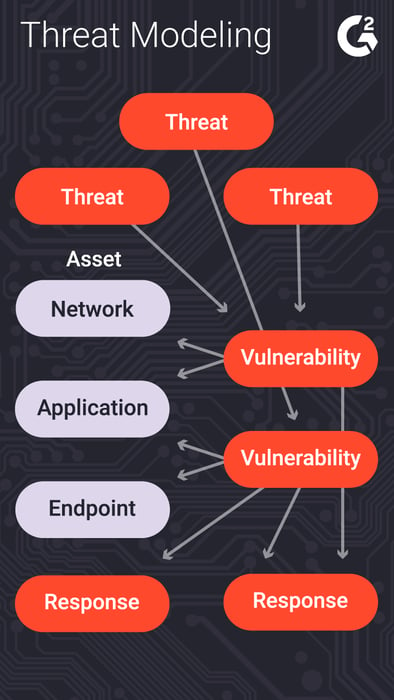 learn.g2.com
learn.g2.com
threat model modeling examples what top
HIDS Vs NIDS —What’s The Difference And Why Should I Care? | By
 medium.com
medium.com
About Me — Justin Tasset
 www.justintasset.com
www.justintasset.com
Harrisresume 19 | PDF | Free Download
 www.slideshare.net
www.slideshare.net
Stereotype Threat: 15 Examples, Definition, Criticisms (2025)
 helpfulprofessor.com
helpfulprofessor.com
Threat Modeling Explained: A Process For Anticipating Cyber Attacks
cyber threat modeling security attacks process system getty cyberattack anticipating explained threats tracking
4 Common Cyber Attacks [Infographic]
![4 Common Cyber Attacks [Infographic]](https://www.yardsticktechnologies.com/wp-content/uploads/2021/05/Copy-of-4-Common-Types-of-Cyber-Attacks-Infographic-.png) www.yardsticktechnologies.com
www.yardsticktechnologies.com
attacks
Cybersecurity Threat Cartoon Vector Illustration | CartoonDealer.com
 cartoondealer.com
cartoondealer.com
VR Headsets Explained: A Beginner's Guide To How They Work - YouTube
 www.youtube.com
www.youtube.com
Threat Modeling: 12 Available Methods
 insights.sei.cmu.edu
insights.sei.cmu.edu
What Is Stereotype Threat | Explained In 2 Min - YouTube
 www.youtube.com
www.youtube.com
stereotype threat
HIDS Vs NIDS —What’s The Difference And Why Should I Care? | By
 medium.com
medium.com
Insider Threats: Risks, Identification And Prevention
 threatcop.com
threatcop.com
Intrusion Detection VS Prevention Systems: What's The Difference?
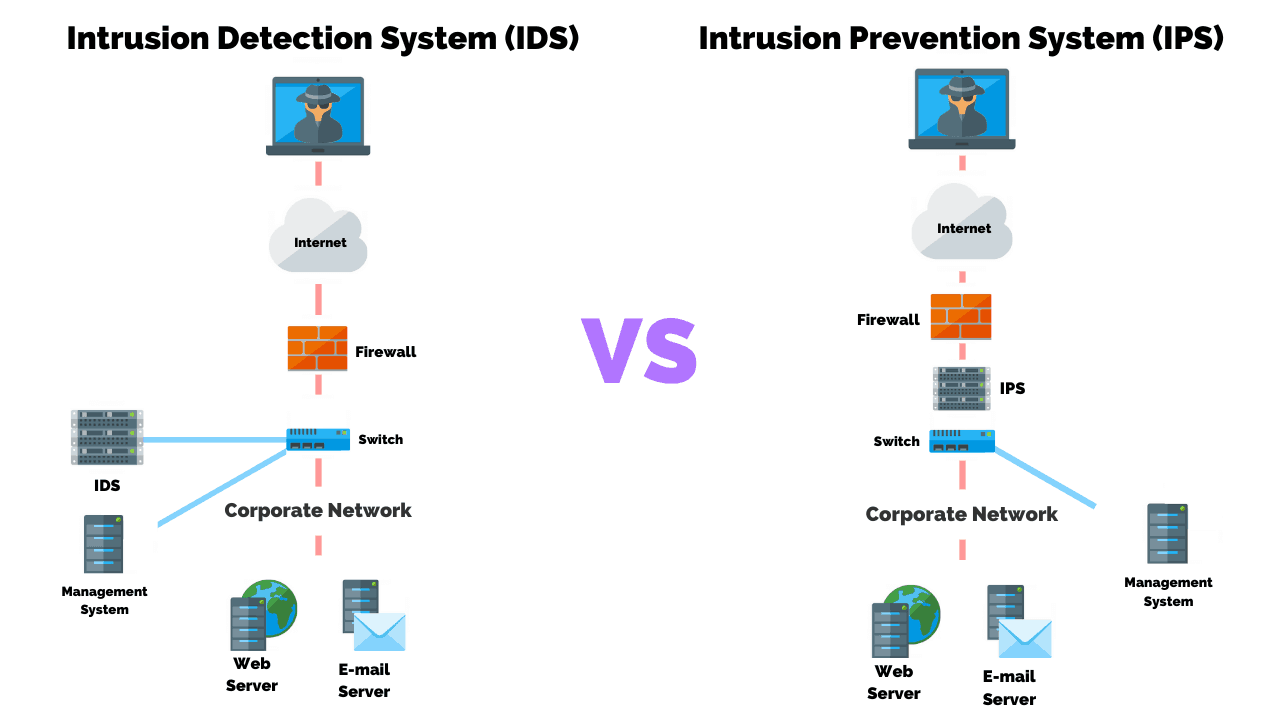 purplesec.us
purplesec.us
My Business Just Experienced A Cyber-Attack! • Total HIPAA Compliance
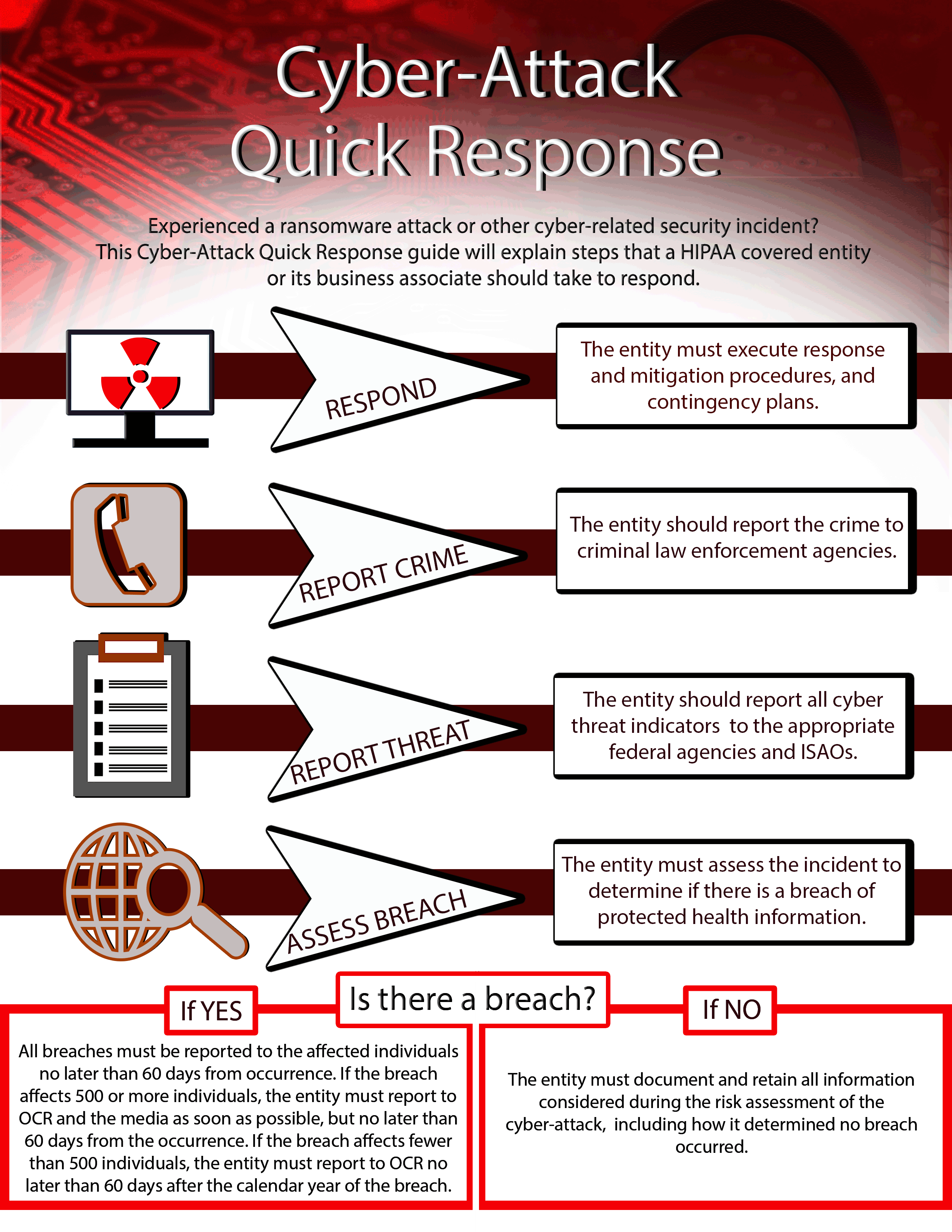 www.totalhipaa.com
www.totalhipaa.com
infographic cyber attack response cybersecurity quick checklist security hipaa hhs business attacks experienced just guidance us review
Understanding Security: HIDS Vs. NIDS Explained - YouTube
 www.youtube.com
www.youtube.com
Comparison Between NIDS And NIPS Cybersecurity Framework
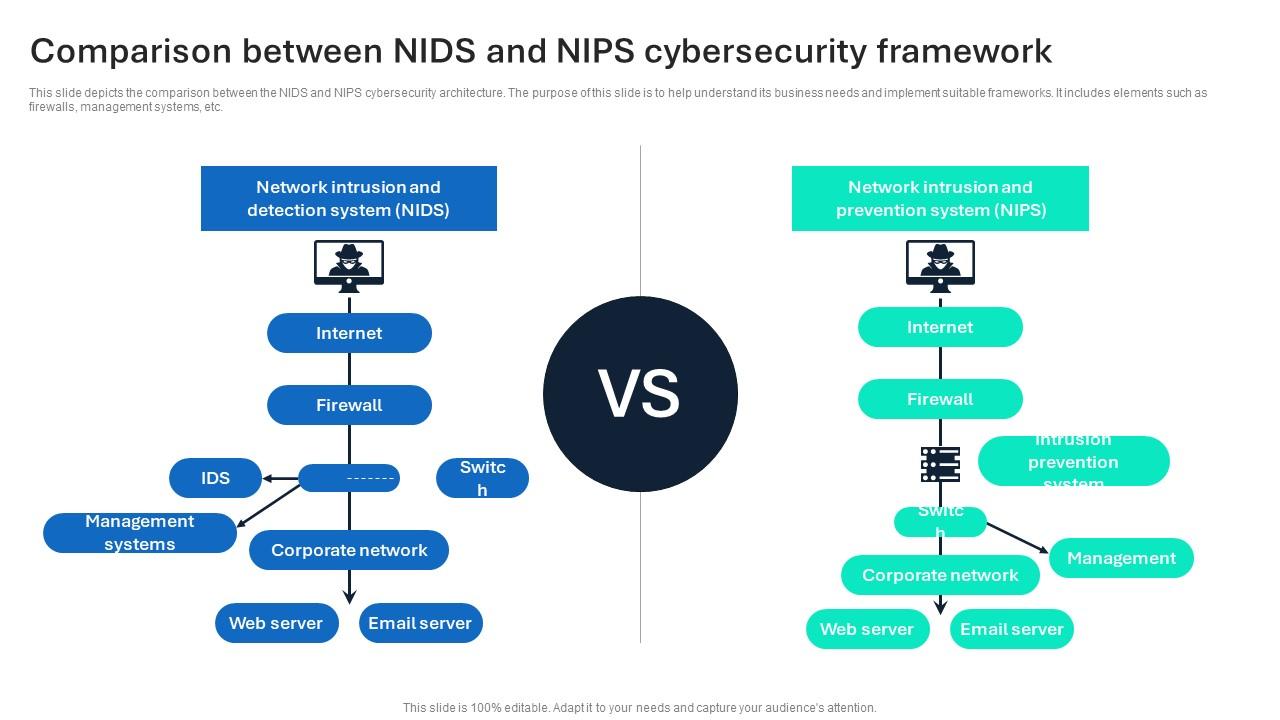 www.slideteam.net
www.slideteam.net
Every Cybersecurity Threat Explained - YouTube
 www.youtube.com
www.youtube.com
Zero-Day Exploit Defense: Cybersecurity Insights
 packetlabs.com.au
packetlabs.com.au
HIDS Vs NIDS —What’s The Difference And Why Should I Care? | By
 medium.com
medium.com
Cybersecurity Threat Cartoons Royalty Free Vector Image
 www.vectorstock.com
www.vectorstock.com
cybersecurity threat cartoons vector license
OWASP Threat And Safeguard Matrix (TaSM) | OWASP Foundation
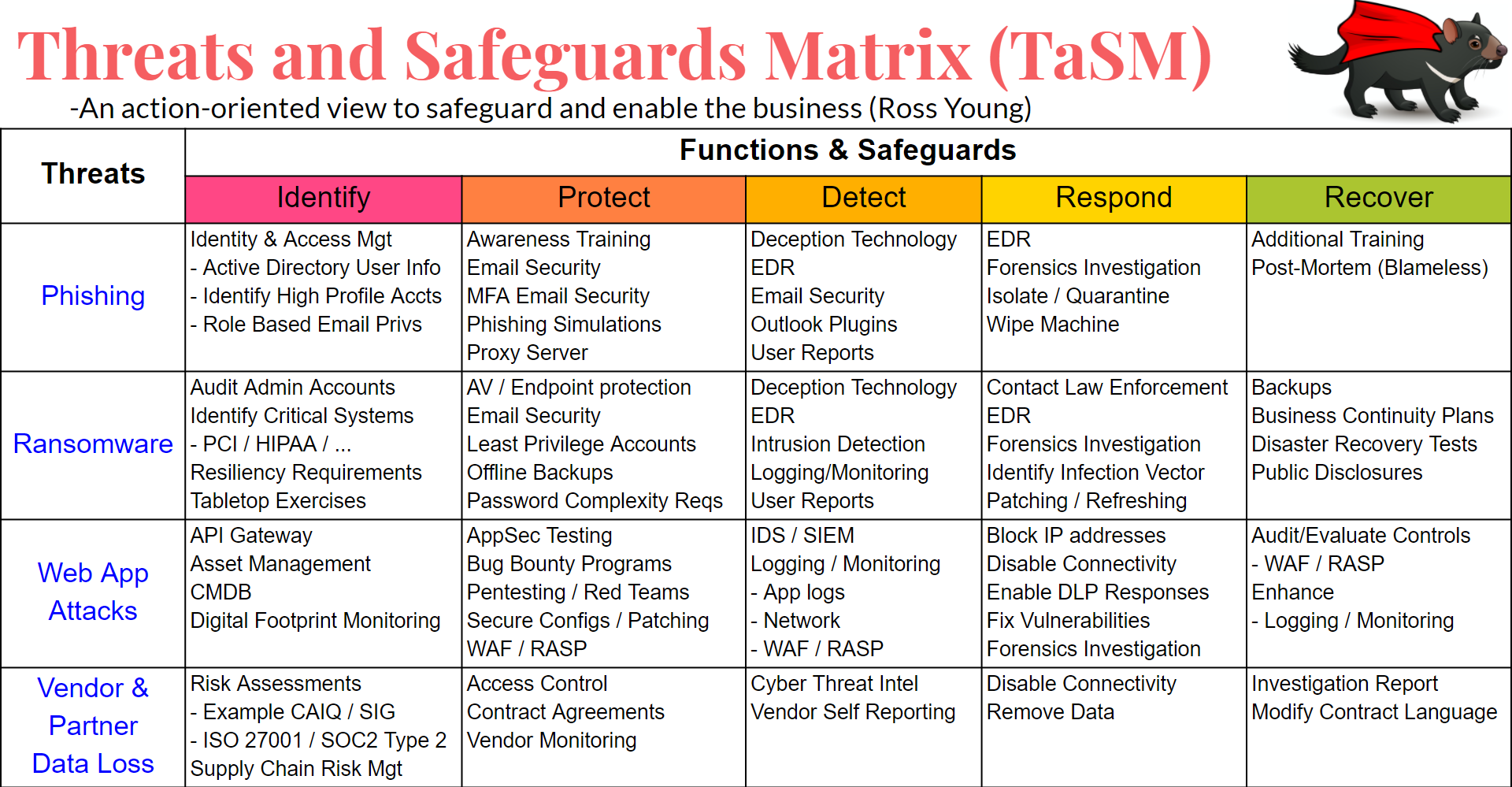 owasp.org
owasp.org
matrix threat owasp safeguard tasm security defense example data threats plan company assets one
Nids: jamaica's controversial nids system explained. About me — justin tasset. Hids vs nids —what’s the difference and why should i care?